Blog
- All Post
- Blog
- Cyber Security
- Uncategorized
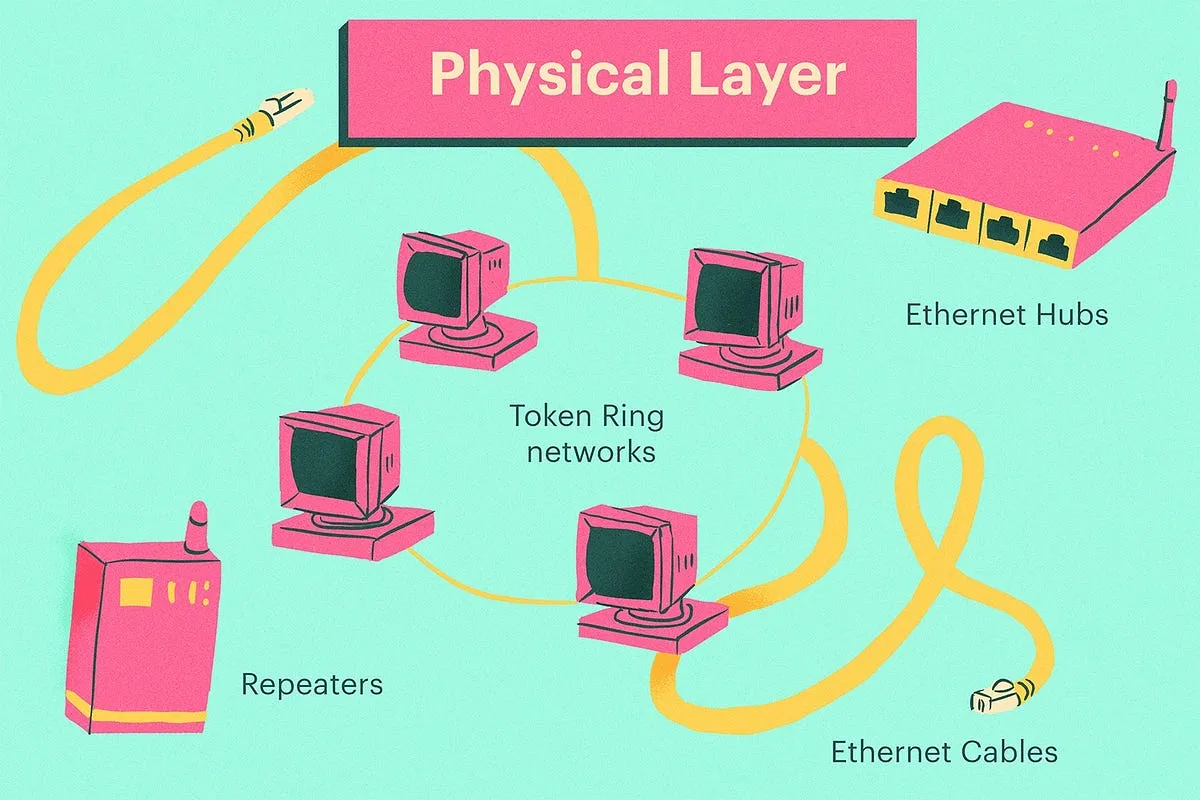
Great! Now that you understand how the different layers of the OSI model work together, let’s dive deeper into one…
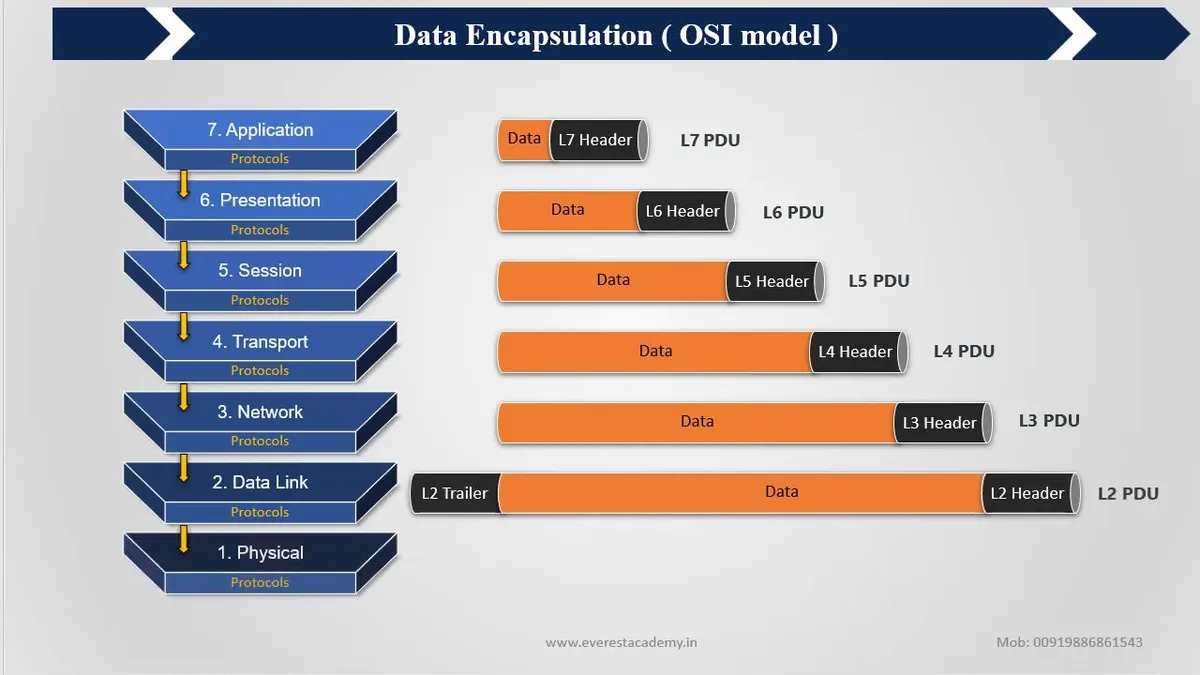
The OSI (Open Systems Interconnection) model was developed by the International Organization for Standardization (ISO) in the late 1970s and…

DNS, or Domain Name System, is the telephone book of the internet. It translates human-readable domain names, like www.example.com, into…

Slamm Technologies Limited – a leading global Information Technology (IT) services provider – has partnered with AmaliTech Ghana Limited to…
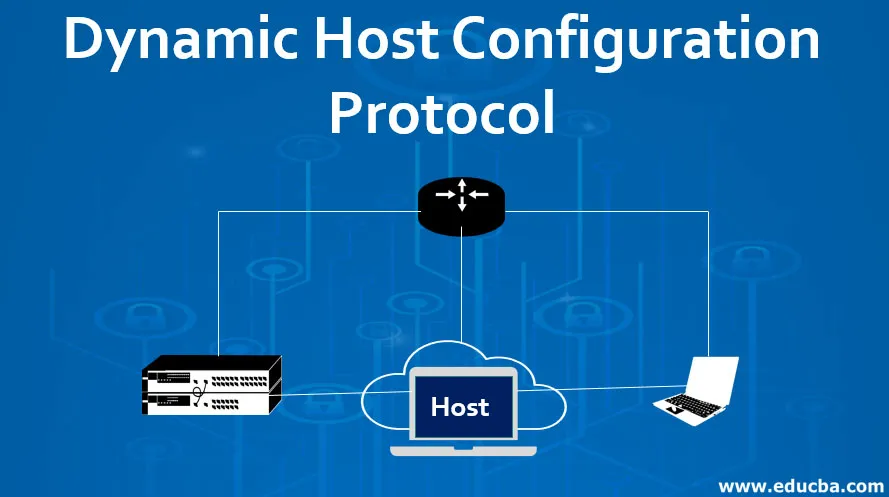
DHCP, or Dynamic Host Configuration Protocol, is like a superhero for your network! It takes care of automatically assigning IP…

Today, we’ll be discussing techniques used in cryptography, which will help you understand how information is secured in today’s digital…

At the beginner level, you will learn the basics of cryptography, such as the meaning of terms like algorithms, keys,…

TCP/IP is a protocol that requires a little bit of knowledge to configure the systems properly. When you configure TCP/IP,…
Now, I know what you might be thinking — “What in the world is a security control?” Well, it’s basically…


